Test your current internet speed
Before you get started, test your current internet speed. Use your speed test result as a baseline and compare the results as you go through your journey on reaching a faster internet connection.
SpeedtestForward proxies play a crucial role in the world of online communication and security. These powerful tools offer users a range of benefits, from enhanced privacy to overcoming geographical restrictions.
In this article, we’ll delve into the intricacies of forward proxies, exploring how they work, their benefits, types, and much more.
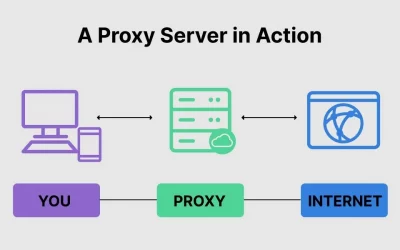
Forward proxies, also known as web proxies, act as intermediaries between a user’s device and the internet. Their primary purpose is to forward requests and responses, effectively masking the user’s IP address. This not only provides an additional layer of privacy but also serves as a valuable tool for various online activities.
How Forward Proxies Work
The functioning of forward proxies involves intercepting and forwarding communication between the user and the internet.
When a user sends a request, it goes through the forward proxy, which then forwards the request to the target server. The server responds to the proxy, which, in turn, sends the response back to the user.
This process helps in hiding the user’s actual IP address.
Benefits of Using Forward Proxies
Forward proxies offer several advantages, making them popular among internet users. One key benefit is enhanced privacy. By masking the user’s IP address, forward proxies make it challenging for websites to track and trace online activities. This added layer of anonymity is particularly valuable for individuals concerned about their privacy on the internet.
Another notable advantage is the ability to bypass geo-restrictions. Many websites and online services restrict access based on geographical locations. Forward proxies can help users overcome these restrictions by providing a different IP address, making it appear as though the user is accessing the internet from a different location.
In addition to privacy and bypassing restrictions, forward proxies contribute to improved security. They act as a barrier between the user’s device and potentially harmful websites or content, preventing direct communication and reducing the risk of cyber threats.
Types of Forward Proxies
Forward proxies come in different types, each serving specific purposes.
Transparent proxies, anonymous proxies, and distorting proxies are the three main categories.
- Transparent proxies: These proxies do not alter the user’s request but provide additional information, such as the user’s IP address.
- Anonymous proxies: These proxies conceal the user’s IP address but may reveal that a proxy is being used.
- Distorting proxies: Similar to anonymous proxies, distorting proxies provide a false IP address, creating confusion about the user’s actual location.
Choosing the Right Forward Proxy for Your Needs
Selecting the right forward proxy depends on various factors, including the user’s specific requirements and preferences. Some popular forward proxy services include ProxyMesh, Luminati, and Oxylabs. When choosing a forward proxy, consider factors like speed, reliability, and the level of anonymity provided.
Setting Up a Forward Proxy
Setting up a forward proxy may seem daunting, but with the right guidance, it’s a manageable process.
Here’s a step-by-step guide to help you get started:
- Choose a reliable forward proxy service: Research and select a forward proxy service that aligns with your needs.
- Configure your device or browser: Follow the instructions provided by the forward proxy service to set up the proxy on your device or within your browser settings.
- Test the connection: Ensure that the proxy is working correctly by accessing a website and verifying your IP address.
Common challenges in setting up forward proxies include compatibility issues and potential conflicts with firewalls. If you encounter any issues, refer to the documentation provided by the proxy service for troubleshooting.
Forward Proxies in Business
Forward proxies are not only beneficial for individual users but also play a significant role in the corporate world.
Many businesses use forward proxies to enhance network security, control internet usage within the organization, and monitor online activities.
By routing all internet traffic through a forward proxy, companies can implement restrictions and safeguards to protect sensitive data and maintain a secure online environment for employees.
Challenges and Risks Associated with Forward Proxies
While forward proxies offer numerous advantages, it’s essential to be aware of potential challenges and risks.
Some drawbacks include:
- Slower Internet speed: The use of forward proxies can sometimes result in slower internet speed due to the additional steps involved in routing traffic.
- Dependency on proxy service reliability: If the chosen proxy service experiences downtime or disruptions, it can impact your internet connection.
- Potential misuse: Forward proxies can be misused for illegal activities or to bypass security measures, leading to potential legal consequences.
To mitigate these risks, users should carefully choose a reputable forward proxy service and adhere to ethical practices.
Comparison with Reverse Proxies
It’s crucial to distinguish between forward proxies and reverse proxies, as they serve different purposes. While forward proxies act on behalf of users, reverse proxies work on behalf of servers.
Understanding the differences between the two helps in determining when to use each type effectively.
When to use forward proxies:
- Enhanced privacy: Forward proxies are ideal for users seeking increased privacy and anonymity.
- Bypassing restrictions: Forward proxies help overcome geographical restrictions imposed by websites or services.
When to use reverse proxies:
- Load balancing: Reverse proxies distribute incoming traffic across multiple servers, optimizing performance.
- Web application security: Reverse proxies can provide an additional layer of security by protecting servers from direct exposure to the internet.
The Role of Forward Proxies in Web Scraping
Web scraping, the process of extracting data from websites, often involves the use of forward proxies. For businesses and researchers engaged in data extraction, forward proxies offer a means to access and collect information without revealing their identity.
However, it’s crucial to approach web scraping ethically and responsibly, respecting the terms of service of websites and ensuring data privacy compliance.
Best Practices for Using Forward Proxies
To make the most of forward proxies, follow these best practices:
- Choose a reputable proxy service: Research and select a forward proxy service with a proven track record of reliability and security.
- Regularly update configurations: Keep your forward proxy configurations up to date to ensure optimal performance and security.
- Monitor usage: Regularly check and monitor the usage of the forward proxy to identify any unusual or suspicious activity.
- Educate users: If implementing forward proxies in a business or organizational setting, educate users about proper usage and potential risks.

The visionary founder behind SpeedtestGo, an innovative platform dedicated to helping users measure and optimize their internet speed. With a deep-rooted love for technology and a mission to empower individuals with reliable internet connections, Shawn has created a remarkable space where users can test their internet speed and gain valuable insights and information through engaging blog content.



![Top 10 School Bypass Proxies Methods: Unblock Any Website [Ultimate Guide]](https://speedtestgo.com/wp-content/uploads/2023/12/Top-10-School-Bypass-Proxies-Methods-400x250.jpg)